Hey there! Are you on the lookout for a trustworthy and well-protected wallet to safeguard your crypto assets? Look no further! In this blog post, we'll be discussing why Trezor Wallet stands out as an apt choice for crypto maniacs like yourself. With its robust and resilient security facets, easy-to-navigate interface, and commitment to privacy, Trezor Wallet is the go-to option for storing your digital assets safely. Let's dive into the exploration of what you can get after Trezor login and why it deserves a top spot in your trading toolkit!
Trezor Wallet in a nutshell
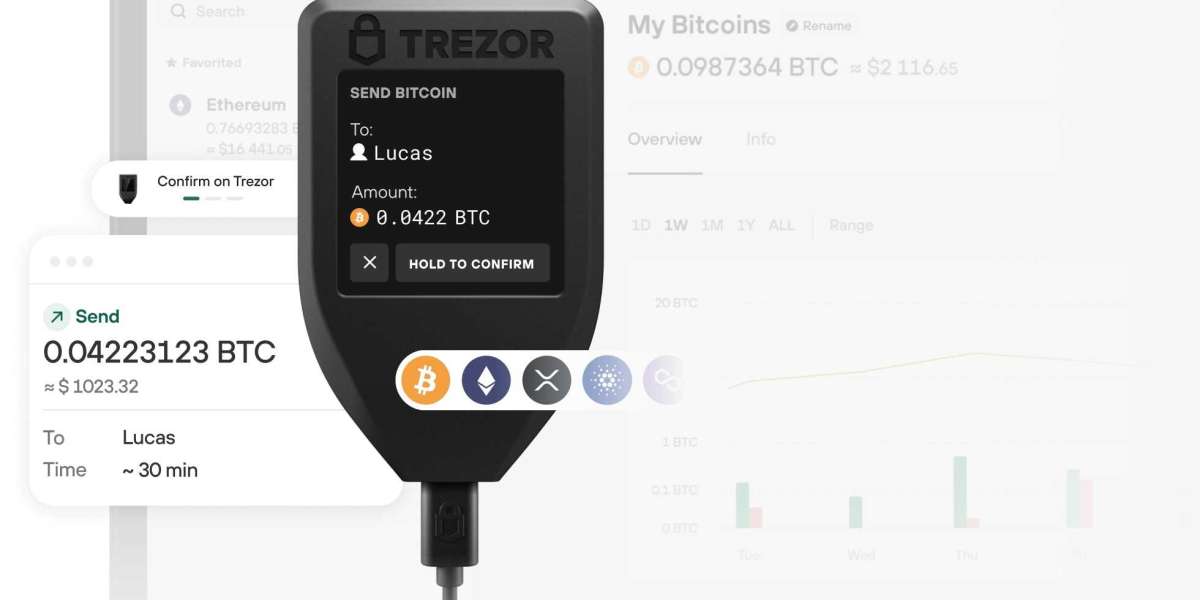
Trezor Wallet is a hardware wallet that allows its users to go offline and store crypto assets. This wallet is also manageable online with the Trezor Suite application which requires a secure Trezor login to go. Some key facets of this wallet are its secure recovery through the wallet’s seed phrase, PIN, and Passphrase to enter into the wallet and its open-source design. I’m going to present a cumulative summary of some more beneficial features of the Trezor Wallet. Let’s move on further to deep dive into the details.
What you can receive after Trezor login?
- Robust Security Measures
When it comes to protecting your crypto assets, the security of the assets is the name of the game. Trezor Wallet takes security to the next level with its industry-leading robust security facets. The wallet implies state-of-the-art hardware end-to-end encryption, ensuring that your purchased keys are kept offline safely and out of reach from potential scams and threats. Software wallets are more at risk than hardware ones. To diminish the risk of hacking and phishing attacks, you can store your keys after Trezor login securely.
- User-Friendly Interface
Ease of use interface is another field where Trezor Wallet excels. Whether you're a newcomer to the crypto world or an experienced crypto expert, the wallet’s intuitive interface lets you experience a breeze-to-navigate interface. The setup process of the Trezor Wallet is quite straightforward, a PIN is needed for Trezor login. The clear and concise display of the Trezor device ensures that you can easily verify transactions and confirm addresses. Trezor Wallet also gives you the freedom to store and manage multiple assets all under one platform.
- Privacy and Anonymity
Trezor Wallet values privacy concerns and provides complete control over your personal info and funds. Your data available on the Trezor platform remains confidential and accessible through Trezor login. Transactions can be securely initiated through this device and signed without disclosing any personal information outside. This emphasis on privacy term ensures that your crypto activities and data remain anonymous and mitigates the chances of potential data breaches that could compromise your identity.
- Continuous Development and Support
Trezor Wallet is securely backed by a dedicated team of developers who constantly serve to enhance the wallet’s features and security measures. Regular firmware and wallet updates keep the wallet up to date with the latest industry trends and security standards. Trezor's active support community ensures that any quest or Trezor login issues you may have are promptly addressed.
The Final Take!!
In a fast-paced evolving digital landscape, securing your crypto assets is crucial. Trezor Wallet emerges as the perfect solution, offering robust security, user-friendly functionality, privacy, and ongoing development support. With Trezor login, you can confidently store and organize your digital assets as you know that your funds are secure from external threats. So, why wait? Embrace the power of Trezor Wallet and take complete control of your crypto holdings right now!